Securing your WordPress site against SQL injection attacks is necessary to safeguard your data and maintain your visitors’ trust.
SQL injection is a common technique used by hackers to attack your database. Once they do that, hackers can read your sensitive data, modify it, and take control of your entire database.
To protect your website from this threat, it’s crucial to implement strong security measures on your website.
At WPBeginner, we take security very seriously and have gone above and beyond to protect our site from hackers and malware. Many of the security practices we recommend against SQL injection attacks are methods we have successfully used ourselves.
In this article, we will share some actionable tips to prevent SQL injection attacks in WordPress, step by step.

Why Prevent WordPress SQL Injection Attacks?
SQL stands for Structured Query Language, which is a programming language that communicates with your WordPress site’s database. Without this feature, your site cannot generate any dynamic content.
However, unauthorized user input, outdated software, or revealing sensitive information can cause security vulnerability and make it easy for hackers to perform SQL injection attacks.
This attack targets your database server and adds malicious code or statements to your SQL. Upon doing that, hackers can use sensitive information stored in your database like user data for identity theft, account takeover, financial fraud, and more.
They can also change database entries or account permission and perform DDoS attacks, making it difficult for actual users to visit your website.
This can damage customer trust, negatively impact user experience negatively, and decrease website traffic, which will be bad for your small business growth.
Having said that, let’s take a look at some actionable tips that can prevent SQL injection attacks in WordPress. Here’s a quick overview of what we’ll talk about in this article:
- Perform Site Updates Regularly And Use a Firewall
- Hide Your WordPress Version
- Change the WordPress Database Prefix
- Validate User Data
- Limit User Role Access and Permissions
- Create Custom Database Error Messages
- Remove Unnecessary Database Functionality
- Bonus: Use WPBeginner Pro Services to Create a Secure Site
Note: Before you make any changes to your database for preventive measures, we recommend creating a backup for it. This way, if anything goes wrong, you can use the backup to fix it. For details, see our tutorial on how to make a WordPress database backup manually.
1. Perform Site Updates Regularly And Use a Firewall
An effective way to prevent SQL injection attacks is to regularly update your WordPress site to the latest version. These updates often patch up security vulnerabilities, including database software issues, making it difficult for hackers to attack your site.
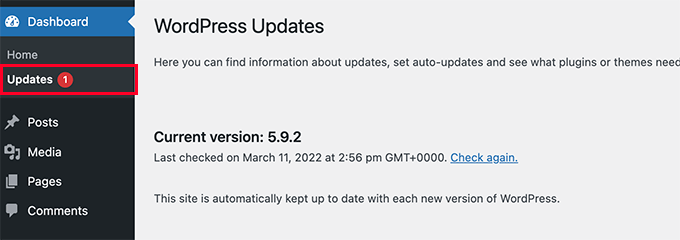
If you are using an outdated version of WordPress, then we recommend enabling automatic updates for the latest version by visiting the Dashboard » Updates page.
Here, simply click the ‘Enable automatic updates for all new versions of WordPress’ link. Now, all the major updates will be installed on your site upon release.
For more information, you may like to see our beginner’s guide on how to safely update WordPress.
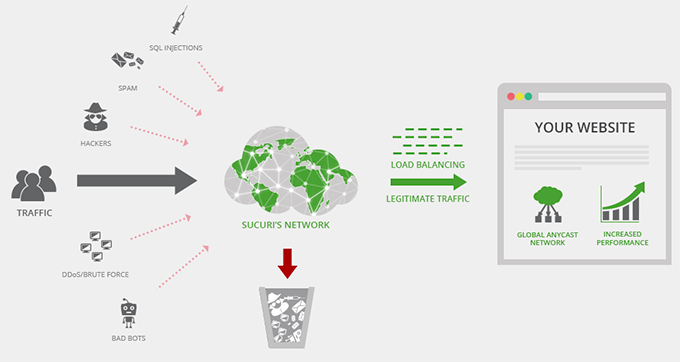
Once you have done that, you can also add a firewall for additional security. This feature acts as a shield between your site and incoming traffic and blocks common security threats, including SQL attacks, before they reach your website.
If you run a small online business, we recommend Sucuri, which is one of the best WordPress firewall software options on the market. It offers an application level firewall, brute force prevention, as well as malware and blacklist removal services, making it a great choice.
We have first-hand experience with the tool. It even helped us block 450,000 WordPress attacks on our website in the past.
That said, Sucuri might not be powerful enough for larger, high-traffic sites. In that case, you might consider Cloudflare, which can give you security features as well as an impressive content delivery network (CDN).
If you’re unsure about which option is best for your website, check out our article on why we switched from Sucuri to Cloudflare or our Sucuri vs Cloudflare comparison.
2. Hide Your WordPress Version
By default, WordPress displays the current version number of the software you use on your website. For instance, if you are using WordPress 6.4, then this version will be displayed on your site for tracking.
However, your version number’s public visibility can create security threats and make it easier for hackers to perform WordPress SQL injection attacks.
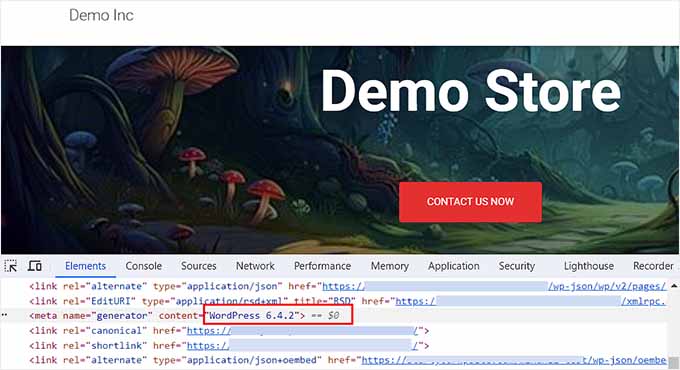
This is because each version of WordPress has its own unique vulnerabilities that attackers can exploit after discovering your version. This will allow them to add malicious code snippets to your site through vulnerable input fields.
You can easily remove the version number from your site by adding the following code snippet to your functions.php file.
add_filter('the_generator', '__return_empty_string');
Once you do that, hackers won’t be able to find your WordPress version number through automatic scanners or any other way.
Note: Keep in mind that a minor error while adding code can make your website inaccessible. That is why we recommend WPCode. It is the best code snippets plugin that makes adding custom code to your site super safe and easy.
For more details, see our tutorial on the right way to remove the WordPress version number.
3. Change the WordPress Database Prefix
By default, WordPress adds the prefix wp_ to all your database files which makes it easy for hackers to plan an attack by targeting the prefix.
The easiest way to prevent SQL injection attacks is to change the default database prefix with something unique that hackers won’t be able to guess.
You can easily do this by connecting your website using FTP. After that, open the wp-config.php file and find the change the $table_prefix line. Then, you can change it from simply the default wp_ to something else like this: wp_a123456_.
$table_prefix = 'wp_a123456_';
Next, you must visit the cPanel of your web hosting account. For this tutorial, we will be using Bluehost. However, your cPanel may look a bit different depending on your web hosting company.
Here, switch to the ‘Advanced’ tab and click the ‘Manage’ button next to the ‘PHPMyAdmin’ section.
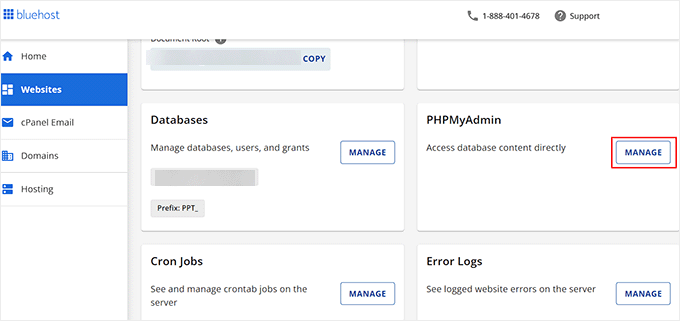
This will open a new page where you must select your database name from the left column and switch to the ‘SQL’ tab from the top.
After that, you can add the following SQL query into the text box.
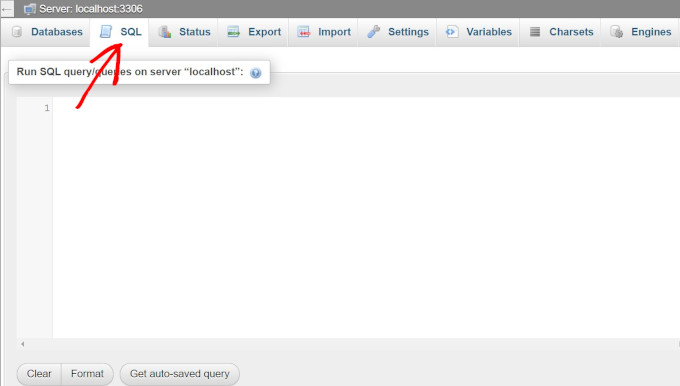
Just keep in mind to change the database prefix to the one that you picked when editing the wp-config.php file.
RENAME table `wp_comments` TO `wp_a123456_comments`;
RENAME table `wp_links` TO `wp_a123456_links`;
RENAME table `wp_options` TO `wp_a123456_options`;
RENAME table `wp_postmeta` TO `wp_a123456_postmeta`;
RENAME table `wp_RENAME table `wp_commentmeta` TO `wp_a123456_commentmeta`;
posts` TO `wp_a123456_posts`;
RENAME table `wp_terms` TO `wp_a123456_terms`;
RENAME table `wp_termmeta` TO `wp_a123456_termmeta`;
RENAME table `wp_term_relationships` TO `wp_a123456_term_relationships`;
RENAME table `wp_term_taxonomy` TO `wp_a123456_term_taxonomy`;
RENAME table `wp_usermeta` TO `wp_a123456_usermeta`;
RENAME table `wp_users` TO `wp_a123456_users`;
For more instructions, you can see our tutorial on how to change the WordPress database prefix to improve security.
4. Validate User Data
Hackers usually inject SQL attacks on your website using fields for entering user data, such as comment sections or contact form fields.
That is why it is important to validate all the data submitted on your WordPress blog. This means that user data will not be submitted on your site if it does not follow a specific format.
For instance, a user won’t be able to submit their form if the email address field does not have the ‘@’ symbol. By adding this validation to most of your form fields, you can prevent SQL injection attacks.
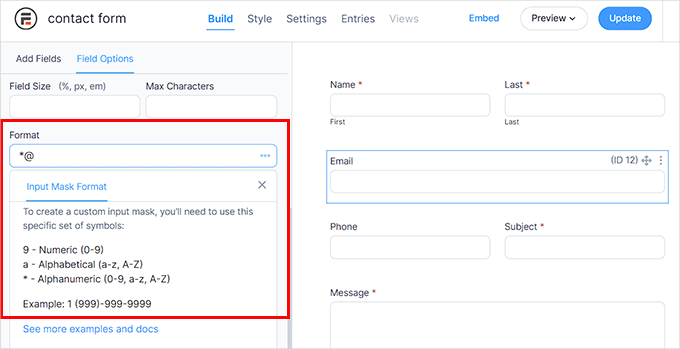
To do this, you will need Formidable Forms, which is an advanced form builder plugin. It comes with an ‘Input Mask Format’ option where you can add the format that users must follow to submit the form field data.
You can add a specific format for phone numbers or single text fields.
If you do not want to validate your form fields, then we recommend WPForms because it is the best contact form plugin that comes with complete spam protection and Google reCAPTCHA support.
It also allows you to add dropdown menus and checkboxes to your forms, making it difficult for hackers to add malicious data.

For more details, see our tutorial on how to create a secure contact form in WordPress.
5. Limit User Role Access and Permissions
Another tip to prevent WordPress SQL injection attacks is to limit user access to your website.
For instance, if you have a multi-author blog, then you will have various authors along with subscribers and administrators. In that case, you can improve site security by limiting the full admin access to the administrator only.
You can restrict all the other user roles to specific functions that they will require to perform their job. This will reduce user access to your database and prevent SQL injection attacks.
You can do this with the free Remove Dashboard Access plugin. Upon activation, simply visit the Settings » Dashboard Access page, where you can decide which user roles get access to the dashboard.
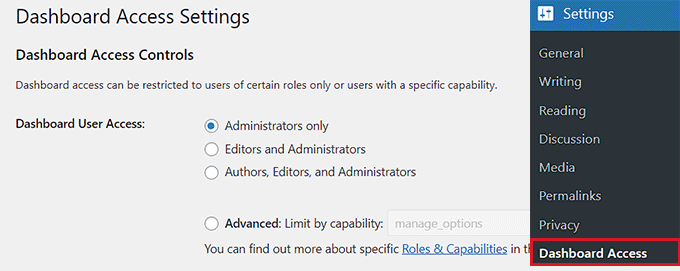
If you want to limit users depending on their capability, then you can see our tutorial on how to add or remove capabilities from user roles in WordPress.
Similarly, you can also limit the authors to their own posts in your admin area for more security.
6. Create Custom Database Error Messages
Sometimes your users may come across a database error on your website, which can display important information about your database, making it vulnerable to SQL injection attacks.
In that case, we recommend creating a custom database error message that will be displayed to users when they come across this common error. To do this, you will need to copy and paste the following content into a notepad app and save the file as ‘db-error.php’.
<?php // custom WordPress database error page
header('HTTP/1.1 503 Service Temporarily Unavailable');
header('Status: 503 Service Temporarily Unavailable');
header('Retry-After: 600'); // 1 hour = 3600 seconds
// If you wish to email yourself upon an error
// mail("your@email.com", "Database Error", "There is a problem with the database!", "From: Db Error Watching");
?>
<!DOCTYPE HTML>
<html>
<head>
<title>Database Error</title>
<style>
body { padding: 20px; background: red; color: white; font-size: 60px; }
</style>
</head>
<body>
You got problems.
</body>
After that, connect your site to an FTP program and upload the file you just created to your site’s /wp-content/ directory.
Now, when users encounter a database error on your website, they will see an error message informing them about the issue without revealing any sensitive information.

Plus, the “Database Error” title will be displayed in the web browser tab.
For more details, see our tutorial on how to add a custom database error page in WordPress.
7. Remove Unnecessary Database Functionality
To prevent SQL injection attacks, you should also try to remove all the database functionality and files that you do not need on your website.
For instance, you can delete unnecessary tables, trash, or unapproved comments that can make your database susceptible to hackers.
To remove unnecessary database functionality, we recommend WP-Optimize. It is an amazing plugin that removes unnecessary tables, post revisions, drafts, trashed comments, deleted posts, pingbacks, post metadata, and so much more.
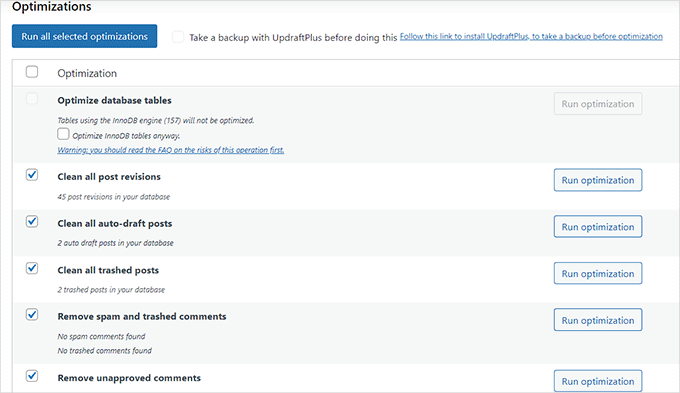
It removes all the files that you do not need and optimizes your database to become more secure and faster. For details, see our beginner’s guide on how to optimize your WordPress database.
Bonus: Use WPBeginner Pro Services to Create a Secure Site
Once you have taken all the preventive measures against SQL injection attacks, you can also opt for WPBeginner Pro Services.
We can help you identify and fix any other security vulnerabilities that you do not know about. Plus, if you have already faced an SQL injection attack, then our experts can help you contain the damage and recover your systems.
You can also hire us to improve your site’s speed optimization, design, SEO, or even completely rebuild your existing WordPress site, whether it’s been hacked or not.
For more information, check out all of our WPBeginner Professional Services.
We hope this article helped you learn how to prevent WordPress SQL injection attacks. You may also like to see our beginners’ guide on how to check for WordPress security updates or our ultimate guide to WordPress security.
If you liked this article, then please subscribe to our YouTube Channel for WordPress video tutorials. You can also find us on Twitter and Facebook.




Moinuddin Waheed
This is new to me that I can easily hide the wordpress version which will by default prevent hackers to guess the vulnerabilities based on wordpress versions and their loopholes.
Great tips to prevent website from SQL injection.
I will implement these tricks to make my website foolproof of any security loophole.
Oyatogun Oluwaseun Samuel
For me, hiding the wordpress version is new to me. Each version of wordpress comes with their own vulnerability so hiding the version number will leave hackers clueless on what version of wordpress is being used talk less of utilising related vulnerabilities, thanks for the head up. I also think if you’re developing plugin that collect users input, it is wise to escape user inputs (after normal validation) that will be inserted into database
Jiří Vaněk
WordPress security is alpha and omega for me. Related to that is SQL, which I’ve never paid much attention to. Thanks for this list of great tips. I’m going to check my blog right away to see what I can improve according to your list. At least I’ll try to hide the version and so on.